Current situation of chain stores
Easy occurrence of robbery and theft incidents
Chain stores are prone to theft and robbery incidents.
Difficulty in managing numerous stores
Chain stores have numerous stores, making it difficult for managers to manage and keep track of each store's situation in a timely manner.
The store was robbed and robbed, causing losses
Theft or robbery of a store can cause serious economic losses and also pose a threat to the safety of store personnel.
Not conducive to the long-term stable operation of the store.
Unable to respond promptly when the case occurred
When robbery and theft incidents occur, there are no timely and effective response measures.
Background of the project implementation plan
With the development of communication technology and the increasing popularity of networks, it has become possible to establish a remote monitoring and early warning system that meets the security requirements of chain stores.
network transmission
With the increasing development, improvement, and popularization of the internet, thousands of households have access to it. Using the internet as a transmission method does not require a significant cost or time to set up the network, and can directly establish a network using the operator's network.
Warning and linkage
The system adopts AI humanoid recognition cameras and wireless alarm probes to cooperate in defense deployment. After deployment, it can detect and link alarms for illegal intrusion targets, and also support emergency button alarms.
centralized management
All store monitoring devices are connected to the server in the management center for unified management. In case of abnormal situations, the on duty personnel can quickly respond and handle them, minimizing economic losses.
Project construction objectives
AI humanoid recognition camera wireless infrared alarm probe
Installing AI intelligent humanoid recognition cameras and wireless alarm probes inside and outside the store for mutual defense, while the cameras have built-in TF cards for all-weather recording, which can provide effective evidence for post event evidence.
Automatic announcement through linked speakers, uploading of police information to the management center
When an alarm occurs, the camera automatically links with the sound column to emit an alarm sound for driving away, and at the same time uploads the alarm message to the management center. At the same time, the wireless alarm probe will also upload the alarm message to the management center when detected, making it convenient for the center to confirm and understand in a timely manner.
TV wall linkage pop-up screen, confirmed and processed by the monitoring center
When the camera and wireless alarm probe trigger an alarm, all cameras in the store can be linked to pop up a screen on the management center's TV wall. After confirmation, the store can shout and activate the smoke evacuation device to drive away intruders. At the same time, store personnel can also trigger the alarm through the emergency alarm button.
Chain Store Security System Solution
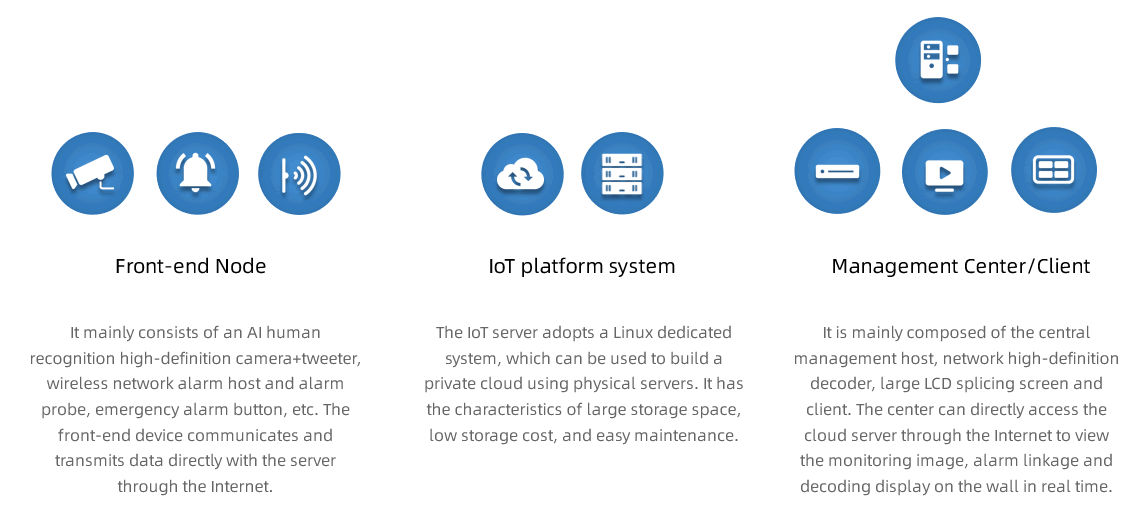
Main components of the system architecture
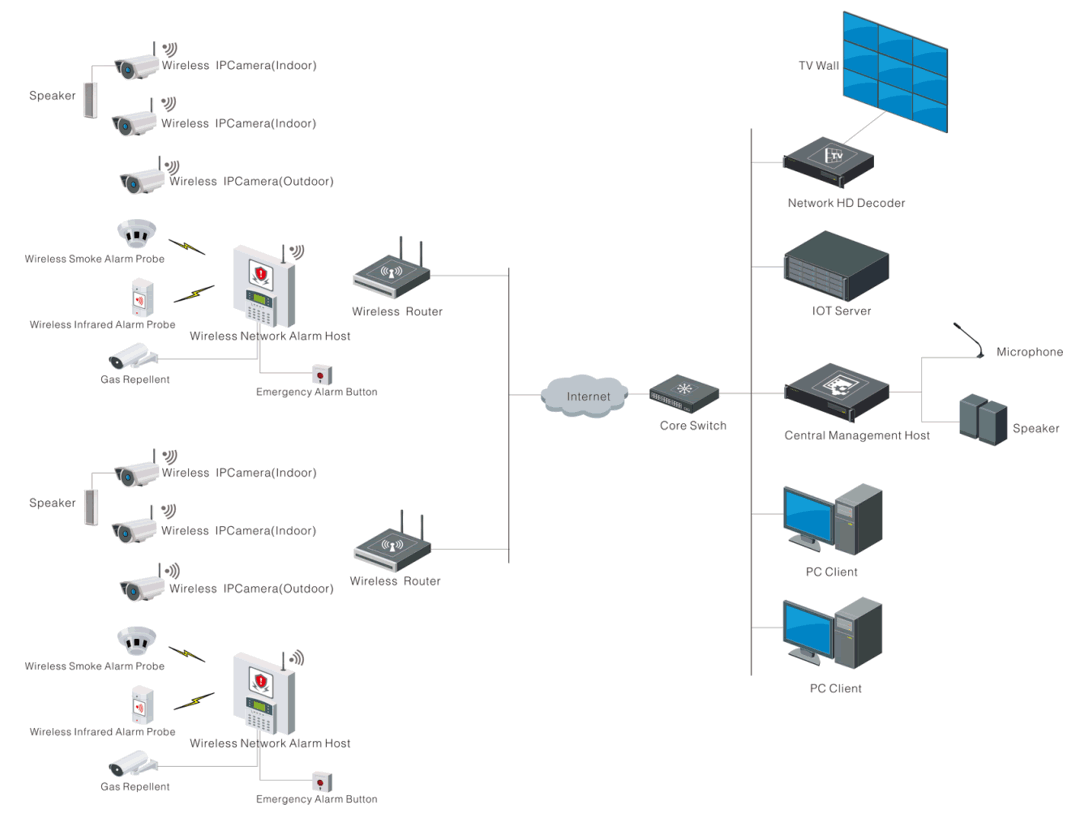
System topology
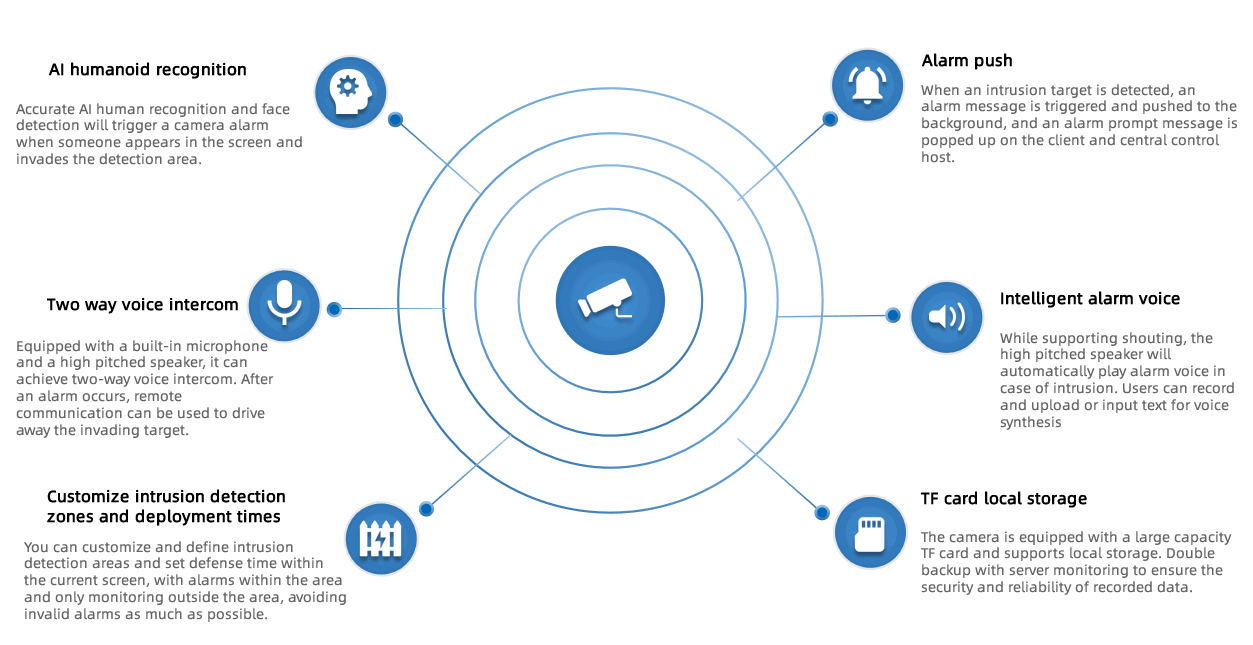
Main technical features of the camera
Main technical characteristics of alarm host

Wireless connection of alarm probe
All alarm probes adopt wireless code connection method, making installation more convenient and configuration more flexible.

built-in battery
The alarm host is equipped with a rechargeable battery, which can still supply the alarm host with power for at least 4 hours after the mains power is cut off.

Upload the alarm message to the monitoring center
The alarm host can be connected to a cloud server and upload alarm messages. It also supports linking client alarm prompt sounds and linking camera images to pop up on the TV wall.
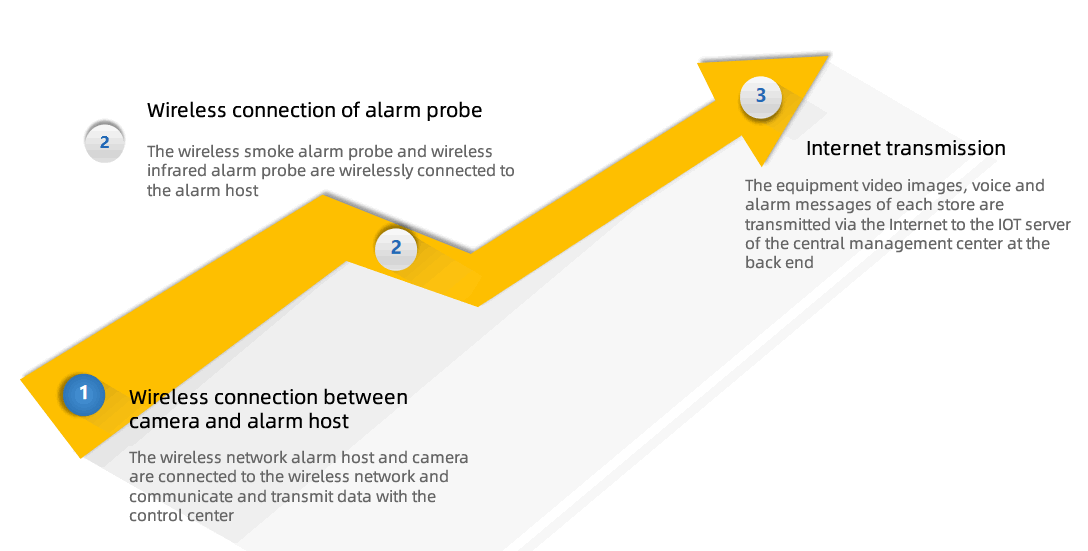
Network transmission method
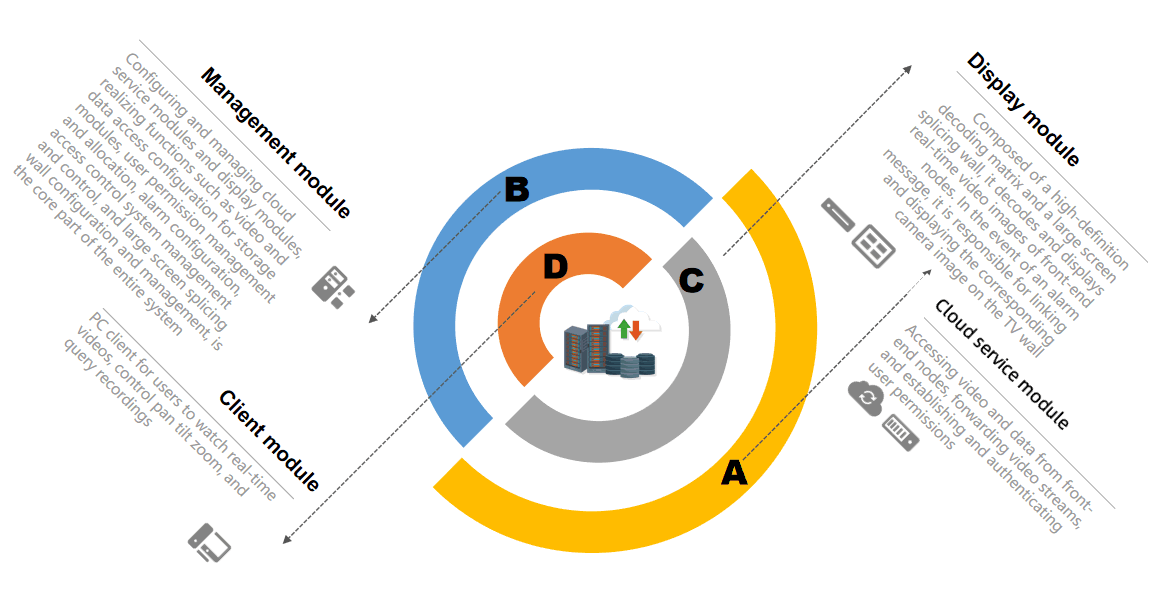
Main components of the management platform system
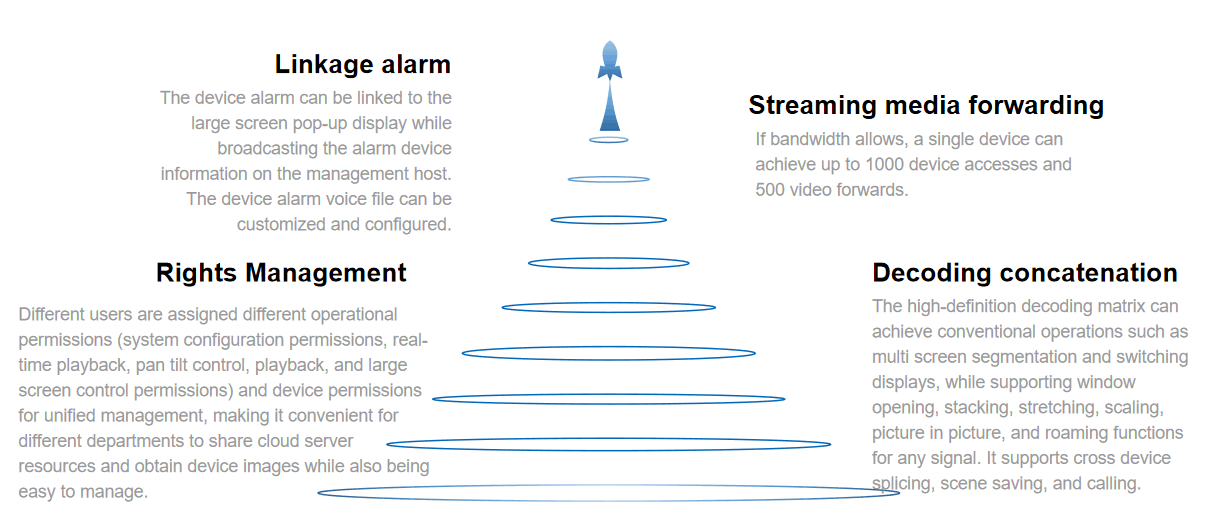
Main technical features of the system management platform
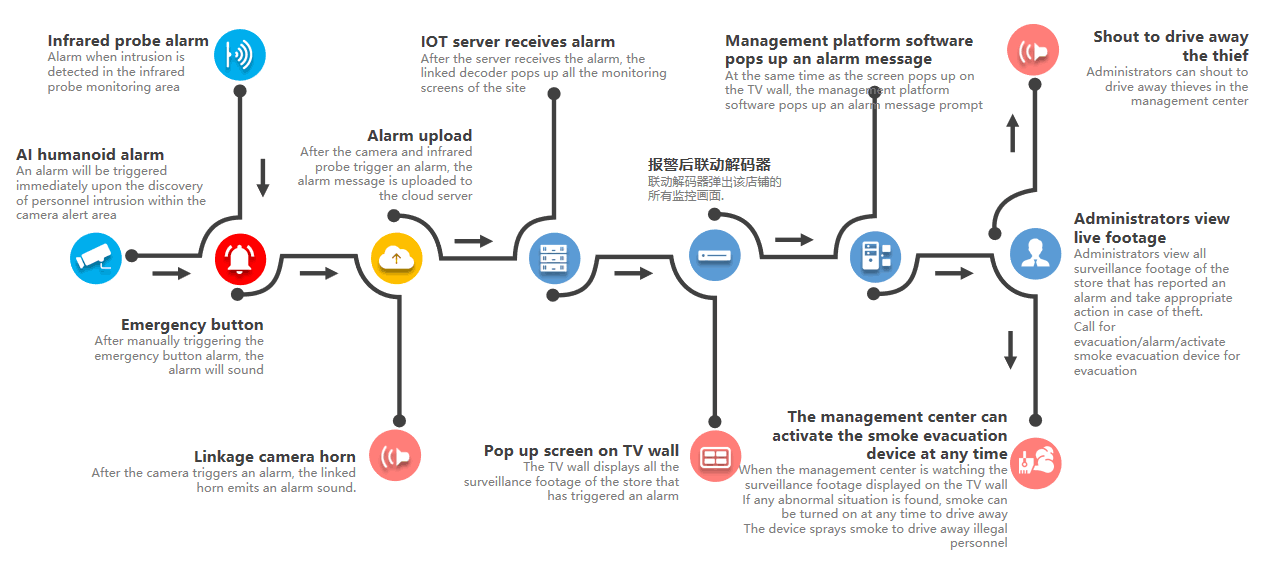
Security system workflow